Two Descent on Elliptic Curve
2025-10-28 | #Crypto #Elliptic Curve
Motivation
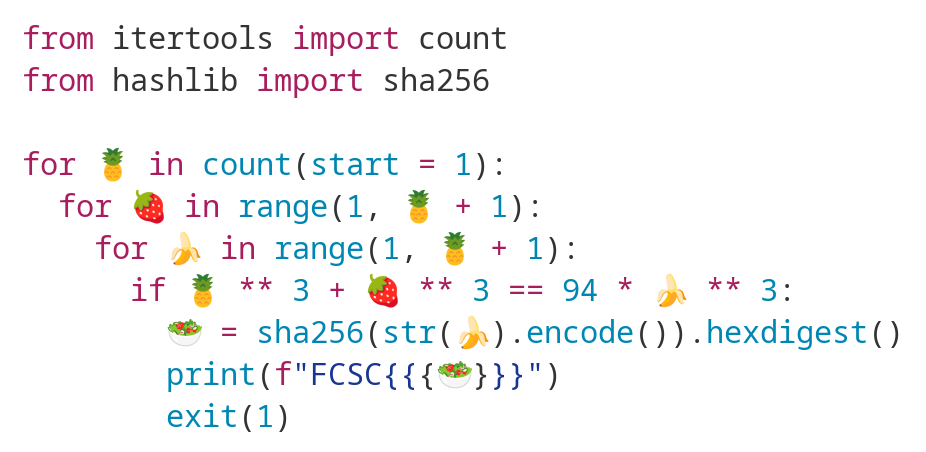
While replaying challenges from prior FCSC, I ended up trying to solve the challenge Surface, in this challenge we just have to solve the following equation over the rationals :
$$\begin{cases} a^2 + b^2 = c^2 \\ ab = 20478\end{cases}$$It turns out that such pair $(a, b) \in \mathbb Q^2$ are called congruent numbers and finding those is equivalent to finding some rational point on an elliptic curve, more specifically :
if $(a, b, c) \in \mathbb Q^3$ is a solution to